My blog concentrates on Microsoft technology with the occasional presence of 3rd party technology when it offers significant advantages over the native MS tools. The use of the KEMP Technologies VLM-200 load balancer with Exchange would be one example.
Auditing Active Directory security is probably another area where 3rd party tools can provide certain advantages for the domain administrator.
By AD security, I am referring to everything from failed logon attempts, locked out accounts, accounts that have not been used in ages, creation of new objects, modifications to existing objects, the addition of users to the domain admins group and so much more.
What native auditing tools do we have?
Essentially Event Viewer.
However, Event Viewer has limitations that may become unacceptable. For example, some events are logged on a single domain controller, so if you have 4 of them (or 40), you would have to search the event logs of several domain controllers. Some readers may remember the limitations in auditing the "LastLogon" attribute and the new and improved "LastLogonTimestamp" attribute.
There is a Microsoft tool called EventCombMT (part of the Account Lockout and Management Tools "suite") that allows administrators to search for events on multiple domain controllers. The tool, with the rest of the tool set, can be downloaded here:
Unfortunately, the tool is only supported on Windows 2000 and 2003 Server domain controllers (see the System Requirements section) which are no longer supported as operating systems. I have been able to make it work on Windows 2008 (and others have as well, apparently) but if you are limited to running supported products only on your domain controllers, this may not be an option. I have not tried it on Windows 2012/R2 at all.
More recently, PowerShell allows us to perform queries for locked out users...
Search-ADAccount -LockedOut -usersOnly | ft Name,LockedOut -auto
and for disabled users...
Get-ADuser -f {Enabled -eq "False"} | fl name
Note: -f is short for -filter.
With short scripts, we can find users whose passwords are about to expire and users who have not logged on recently.
However, these solutions require a certain version of PowerShell (at least version 3) and still may not provide all the auditing features required in a professional environment.
For example, can we receive an email alert when someone is added or removed from the Domain Admins group? Can we receive an alert for anything? What kind of reports can we configure for automatic mailing to a supervisor?
***
I have at least glanced at a number of Active Directory auditing tools. In an excellent but now 5 year old review, Eric B. Rux compared some of the main Active Directory auditing tools on the market:
There are some notable name changes. Beyond Trust acquired Blackbird and their AD auditing product is now called "Power Broker Auditor for Active Directory". Stealthbits acquired NetVision and NVAssess is now "Stealth AUDIT". Dell has acquired Quest but the auditing tools are still marketed under the former name. I've worked with both Power Broker Auditor for Active Directory and ManageEngine's AD Audit Plus tool.
I cannot present all these products and certainly not all the features of each in detail. Using ManageEngine's AD Audit Plus, I will demonstrate how one would install such a product and then some of the features that will enhance the administrator's auditing abilities compared to native Active Directory.
Besides the qualities of the product itself, I've also selected AD Audit Plus for a very simple reason: the ease of setup. As Eric states in his review, AD Audit Plus does not require SQL or even SQL Express. A MySQL database is configured (automatically) in the background. On the other hand, I understand that the product can use SQL if necessary, perhaps in a larger environment.
I'll present the installation of the product, its (basic) configuration and then some features.
I'll present the installation of the product, its (basic) configuration and then some features.
INSTALLATION
The installation of the product for testing on a single domain controller is very easy. However, in a production environment, we would want to install it on a server separate from the domain controllers since it does install, in addition to the MySQL database, a web server which we may not want to run on a domain controller.
I download the trial version from the ManageEngine website and run the executable:
Note: you can click on the images to enlarge them.
At the introduction page, we click on Next,
At the introduction page, we click on Next,
We click on Yes to accept the license agreement...
We can install in the default location:
AD Audit Plus is web-based and installs a web server. This is OK for my test environment but in production, we would install the product on a separate server. This type of scenario (and ensuring high availability for the product) is beyond the scope of this blog post. We can keep the default port or select another more appropriate for our environment:
We can register for technical support at this point (optional).
The product installs:
CONFIGURATION
We first logon with a default account (later we'll configure this so we can logon as a domain administrator).
CONFIGURATION
We first logon with a default account (later we'll configure this so we can logon as a domain administrator).
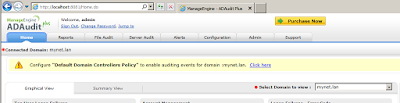
After logging on, I see a message requesting me to click to configure the Default Domain Controllers Policy:
Apparently, all I need to do is click:
Otherwise, we configure the administrative settings under the "Admin" tab, in particular Domain Settings and Technicians:
In "Domain Settings", we see the name of our domain (it seems to have been detected automatically) and a list of domain controllers. Below, I have already added DC2 but we can add more:
Instead of the builtin account used to logon for the first time above, we can add "technicians" (administrators in fact) from the domain we are managing:
That is about all I needed to configure before I could start to evaluate the actual auditing features of the program.
I will add that we can simply open AD Audit Plus by clicking on the icon placed on the desktop (it looks like this):
But also install the product as a service (presumably so it is always running in the background and opens faster). This is one of the options accessible via the yellow warning icon visible in the upper right-hand corner of the management interface:
That is about all I needed to configure before I could start to evaluate the actual auditing features of the program.
I will add that we can simply open AD Audit Plus by clicking on the icon placed on the desktop (it looks like this):
But also install the product as a service (presumably so it is always running in the background and opens faster). This is one of the options accessible via the yellow warning icon visible in the upper right-hand corner of the management interface:
And that's all, at least for an initial evaluation of the product. In my next blog post, I'll have some users connect to the test domain in various scenarios (correct password, incorrect password, incorrect password entered more than the accepted threshold) and see how AD Audit Plus tracks these events.
Thank you for reading the article about Active Directory auditing - 3rd party tools - the example of AD Audit Plus (1) on the blog NEW TECH If you want to disseminate this article on please list the link as the source, and if this article was helpful please bookmark this page in your web browser by pressing Ctrl + D on your keyboard keys.













2 komentar
Good example for ad audit tool. Well explained on the screeshot for what are the steps to be needed.
Balasad audit tool
Great, In this article the concept is very clear and helpful. It describes most valuable information related to active directory auditing with the help of this post such as object access, account logon events, policy change etc. I found nice information related to this from http://www.esystool.com/how-to-enable-active-directory-security-auditing/ which maintain safe and secure active directory environment and track who made changes, when and where.
Balas