Now we must install the ADCS role on our subordinate CA, PKI-Sub-CA-1. As for the root CA, we will add the role using Server Manager. However, many of our choices will be different. I'll open Server Manager and go to the screen where we check the ADCS role:
Note: you can click on the screenshots to enlarge them.
We can read the Introduction to ADCS that follows (no screenshot) and then proceed to the Role Services page. I will select the "Certification Web Authority Enrollment" option:
This is not absolutely necessary: we could distribute certificates solely via Group Policy and not provide a web interface for requesting certificates. However, this allows for certificate requests for non-Active Directory clients.
Note: if we want to automate certificate management for non-Active Directory clients on a large scale, we would have to examine 3rd party products such as MobileIron or VMware Airwatch.
So, in my example, we'll select these two options:
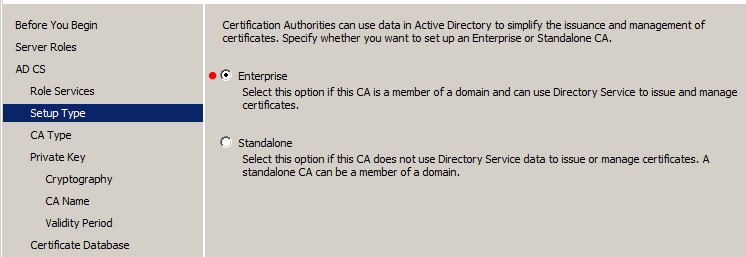
Since PKI-Sub-CA-1 is a domain member, and since we want to be able to use Group Policy to issue certificates (perhaps among other methods), we will select the "Entreprise" option here:
Each CA must have a certificate for itself, either self-signed or issued by another CA. Since PKI-Sub-CA-1 will receive a certificate from the root CA, it will be "subordinate" (to PKI-Root-CA):
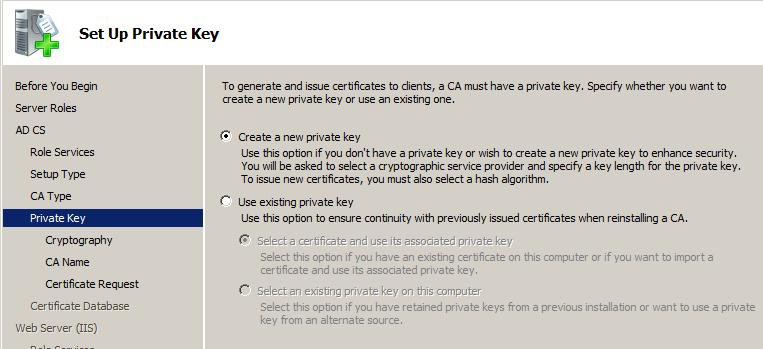
We need a new key:
I will accept the default selections in the Cryptography section:
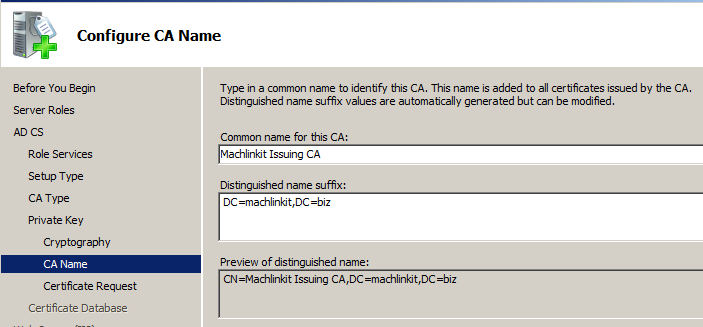
Here, I select a name for the issuing CA:
Note: it is best practice to use a name that is different from the computer name, in this case: PKI-Sub-CA-1. This is for security reasons:
The subordinate CA must request a certificate from the root CA. This is part of the ADCS installation. However, the submission of the request to PKI-Root-CA and the issuance of the certificate will take place in a following section. Since our root CA is offline, we have to save the request as a file that we will copy to the root CA using media appropriate to our circumstances:
We then select the location for the certificate database and log files:
Note: in a real ADCS deployment, we would place the database and log files on separate redundant storage (RAID 1, 5 or 10) and at very least on a different volume than the operating system. Of course, we would want the OS on redundant storage as well. We need to keep in mind the importance of high availability for ADCS. If the CA is unavailable, sooner or later (within hours or days based on your settings), the entire PKI will stop working.
Because I selected the "Certification Web Authority Enrollment" earlier, the Role Services page will display. We can leave the default role services checked and click "Next":
We can review a summary of our choices and if all is well, click on "Install":
The installation finishes but is incomplete. We are reminded that we need to submit the certificate request to the root CA:
Submitting the certificate request to the root CA
So we need to submit the certificate request to the root CA.
First, while still at the subordinate CA, we copy the certificate request file (the location is indicated in the previous screenshot and of course may vary in each environment) to a form of media we can use to transfer it to the root CA.
Once we have copied the request file to the root CA, we open the Certification Authority console, high-light the root CA (PKI-ROOT-CA below), right-click on the icon and select "Submit new request":
Note: we could leave the request file on the media and browse to it directly in the step below.
We then browse to the location of the request file and open it:
This places the request in the "Pending Requests" folder:
We right-click on the pending request, select "All Tasks" and then "Issue":
The issued certificate then appears in the "Issued Certificates" folder:
But now, how do we transport the issued certificate to the subordinate CA that requested it?
We need to open the certificate (double-click for example), go to the "Details" tab and click "Copy to File":
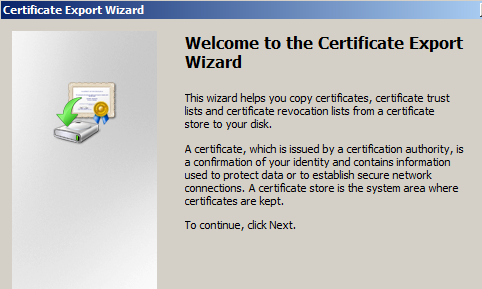
The Certificate Export wizard opens:
We select the .P7B format and check the option to include all certificates in the path:
We select a file location and name:
We click "Next" as needed and then Finish:
We then copy the exported certificate to the removable media and transfer it back to the subordinate CA that made the request.
On the subordinate CA, we open the Certification Authority, designate the CA, right-click, select "Tasks" and then "Install CA Certificate":
We then browse to the exported file and install the certificate:
***
We have almost finished the configuration of the subordinate CA. In the next posts, I will execute a post-installation script and demonstrate the use of "PKI View", a tool that validates certain elements of the PKI environment.
Thank you for reading the article about PKI (Public Key Infrastructure) with ADCS, Part 6: configuration of the subordinate CA (continued) on the blog NEW TECH If you want to disseminate this article on please list the link as the source, and if this article was helpful please bookmark this page in your web browser by pressing Ctrl + D on your keyboard keys.