Below, I have presented the necessary steps to configure Office 365 SSO (Single Sign On) with OneLogin.
Please note that even before completing what follows (but after completing the steps in my two previous blog posts), I was able to connect to Office 365 via the OneLogin website, although SSO was not yet functional.
Indeed, I had to enter my credentials a second time to connect to OneLogin. Once connected, I could click on the Office 365 icon and connect to Office 365 - this time without (re-)entering credentials.
I used the these directions as a guide:
I used the these directions as a guide:
CONFIGURING DESKTOP SSO
***
First, I want to enable SSO. I accomplish this by logging on to the OneLogin website at www.onelogin.com and going to "SETTINGS | Desktop SSO":
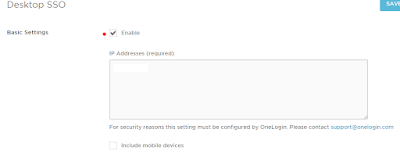
The next step (below) requires the assistance of OneLogin tech support. We check the option "Basic Settings - Enable" and inform OneLogin of the IP address(es) of our local site (or sites). Someone from OneLogin will enter the IP address(es) that will display in the text box below (mine have been edited out for confidentiality):
Note: mobile devices are not present in my test environment so I did not check the last option. Contact OneLogin tech support for more information.
We then enter the "redirect URL" that OneLogin will consult when a request for authentication is made, apparently using the connection established by the server running the Active Directory Connector (ADC). Indeed (and after "http://), we enter the name of the ADC server (simply "ADC" in my case), followed by the port and then "/onelogin/idp". So...
http://ADC:8080/onelogin/idp
Note: steps 1 and 2 (in the screenshot above) refer to a script and documentation to modify Windows Authentication. I was able to make SSO work by simply entering the URL (no need for the script). The script seems to be most useful if you want to use IIS in a scenario presented in this OneLogin document (with a comments section):
CONFIGURING DESKTOP SSO USING A REMOTE AUTHENTICATION SCRIPT IN IIS
As for the Account ID and Remote Token, these two boxes were already populated for me. I have edited out the values for confidentiality.
There is one very important remark to make at this point. Once Desktop SSO is enabled, you may not be able to logon to OneLogin directly with the credentials used to create your OneLogin account. This is because OneLogin now refers authentication requests to your on-premises Active Directory via the server with the Active Directory Connector. If the user does not exist in Active Directory, logon will fail.
There is a solution. Connect to OneLogin using the following type of URL...
https://yourdomainname.onelogin.com/login?remote=off
Where your domain would be the name of your domain minus the .com, .org, .edu or .net (etc.) at the end. Using the well-known fictitious Microsoft domain "contoso.com", that would be:
https://contoso.onelogin.com/login?remote=off
So contoso without the .com.
***
The steps outlined above enable SSO. I will present the user experience in a later blog post.
The following steps seem improve the SSO experience. When I attempted to login to Office 365 (via OneLogin) using a web browser (IE 11), I was not required to re-enter my credentials at any time (the initial login to my Windows desktop client machine was enough). However, the Office 365 logon portal displayed and there was a perceptible delay at this point, even though, ultimately, the logon process to O365 completed with no further manual intervention on my part.
After completion of the following steps, there was no delay at the Office 365 logon portal. The process seemed more efficient, more "streamlined". One of the steps also enables provisioning Office 365 via OneLogin rather than DirSync (the native Microsoft tool).
Note: this is optional. You can use DirSync if you prefer. Consult the documentation for the advantages and disadvantages of the respective options.
Note: this is optional. You can use DirSync if you prefer. Consult the documentation for the advantages and disadvantages of the respective options.
I used these directions as a guide for the next steps:
Note: take notice of the pre-requisites listed in the "Before you begin" section.
If you are not familiar with OneLogin and SSO, it might be best to start with this article and then follow the "Next Topic" link at the bottom of each page for a complete overview of the process:
Introduction to Office 365 Integration with OneLogin
So I log on to the OneLogin site (use the alternate URL presented above if necessary) and go to the APPS tab where I select Office 365. This displays the screen below, which includes several tabs as well. I first go to the Configuration tab:
Although I have edited out my personal information above , we would enter:
- Our organization's registered domain, for example: contoso.com
- An Office 365 account name (a global administrator account is recommended).
- The password of this account.
We would use the following format for the "API user name":
A_GlobalAdminAccount@yourSubDomain.onmicrosoft.com
So, using the same fictitious example as above:
globaladmin1@contoso.onmicrosoft.com
We then click on the blue "Connect" button (notice that the default status is "Not Connected" (in red).
That opens the Microsoft Azure assistant (or wizard) where we logon to Office 365...
And grant access OneLogin access to Office 365:
If all goes well, the status of the "API Connection" should change to "Connected" (in green):
Moving to the Parameters tab, we map Office 365 attributes to OneLogin attributes. Three are required and (at least in my case) were already configured by default:
Note: the settings highlighted above are appropriate for the "Active Directory without DirSync" scenario. In fact, I will use OneLogin's provisioning system rather than Microsoft's native DirSync tool (which is an option however). Moreover, you can map other attributes as well. Consult the OneLogin documentation (or tech support) for additional information.
Next, I will adjust settings under the SSO tab.
Note: I will not present all tabs and related information since not all are necessary for the configuration of SSO.
In this section, we will enable WS-Federation with SAML. Go to the SSO tab and read the important notice: ensure that your domain, API username and API password are correct and that you are connected (see Configuation tab):
Then click on "Enable automatic SAML configuration" (above).
The following message displays, essentially reminding us once again that the domain, API username and API password must be correct. Click on continue:
OneLogin federates your account with Office 365:
Note: it can be defederated if necessary.
At this point, we should test the app by attempting to access our email via Outlook or OWA. I'll skip that part here and present it in my next blog post. If I can access email (or another Office 365 feature) then I have finished this task and can click on "Yes. I'm Done":
There is one last section (tab) to configure if we are using OneLogin to provision users in Office 365 rather than using the native Microsoft DirSync tool. This section can be found under the "Provisioning" tab:
Click the "Enable" option (see above) to use OneLogin provisioning.
The other options were already checked by default.
One reminder: if you intend to use OneLogin instead of ADFS and DirSync, disable these services as described in my two blog posts dedicated to these subjects (they precede the series of blog posts on OneLogin). Of course, if you intend to use DirSync, you would leave the option unchecked and would not have disabled directory synchronization in your Office 365 tenant.
***
In my next blog post, I will present the user experience (what the user sees when they attempt to connect to Office 365 via OneLogin).
Thank you for reading the article about Office 365 with OneLogin: Part 3 on the blog NEW TECH If you want to disseminate this article on please list the link as the source, and if this article was helpful please bookmark this page in your web browser by pressing Ctrl + D on your keyboard keys.