Active Directory Federated Services (ADFS) provides one major advantage, Single-Sign On (SSO), but makes availability of the ADFS server an absolute requirement. Authentication to Office 365 (with federated identities) is impossible without ADFS. In such a context, a single ADFS server would be a single point of failure. Therefore, most organizations using Office 365 (with federated identities) will need at least two ADFS servers and most likely at least two ADFS Proxy servers.
If these concepts are not clear, you can consult one of my previous post about ADFS...
As well as these articles:
Note: as I explained in my blog post referenced above, I have not implemented ADFS Proxy servers so we will not examine that aspect any further.
So, if we have two or more ADFS servers, we need to implement a load balancing solution, either Windows Network Load Balancing (WNLB) or a third party load balancer. KEMP, Citrix and F5 are some of the major vendors in this market.
Note: I will not retain "DNS Round Robin" as an acceptable load balancing solution for ADFS - or Exchange - because of its very significant limitations.
In my test network, I will use a Kemp VLM-200 which is actually a virtual load balancer that operates as a ESXi (or Hyper-V) guest.
If you intend to use WNLB, you might want to consult Henrik Walter's blog posts on the subject:
***
As I stated in my blog post about load balancing for Exchange, I will not demonstrate how to install the VLM-200 in ESXi.
Moreover, I will refer the reader to that blog post for information on downloading a template from the KEMP website and then installing it in the VLM-200.
The template for ADFS can be found in the Resources | Documentation section of the KEMP Technologies website.
Once downloaded, the template can be imported just as I imported the Exchange 2010 template in the blog post referenced above.
The template functions "as is" without much additional configuration.
We do have to assign a virtual IP address, install the certificate used by the ADFS server(s) and then designate the ADFS server(s) as "Real Servers", in other words the target servers to which the load balancer directs incoming ADFS authentication requests. Once this is completed, we can adjust DNS records for the ADFS server(s) so they now point to the load balancer.
I'll illustrate these operations with some screenshots below. As a point of clarification, please note that, in my test network, these are the IP addresses related to ADFS:
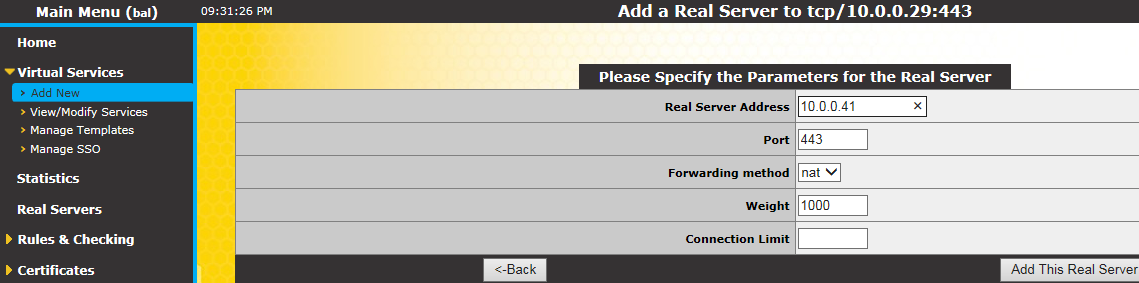
10.0.0.41 -> ADFS server (the "real server" in KEMP terminology)
10.0.0.29 -> VLM-200 (this IP address is different from the VLM-200 management IP)
Of course, in a real network, I would have built a second ADFS server and added it to the list of "Real Servers" in the VLM-200.
***
Assign virtual IP and select ADFS template
We assign a virtual IP address (and port) when we add the "ADFS Internal Farm" virtual service (click on image for a larger view).
This IP address / port combination must be different from other IP / port combinations. We cannot use 10.0.0.28/443 for both Exchange CAS traffic and ADFS traffic. We either need a different IP address or a different port. Since ADFS uses port 443 also, we must use another port.
Also note (above) that this is where we import the "ADFS Internal Farm" template. This template is extremely useful because it configures most of the parameters for the ADFS load balancing service.
Import ADFS certificate
On the ADFS server, we export the 3rd party certificate that was installed on that server and then import it into the VLM-200 certificate store. On the VLM-200, we click on "Import Certificate", browse to the location of the .pfx file (for example "STS-ADFS-export.pfx") and import it, entering the password when prompted. Make sure you assign the certificate to the appropriate virtual service. This is what we should see when we have finished:
Note: it was apparently not necessary to import the intermediate certificates as we had to on the ADFS server itself. Load balancing functions fine without them. I would have imported them but encountered a problem. KEMP Tech Support informed me that they were not necessary. The reader may want to consult KEMP on this matter since results could vary based on firmware or particular configurations.
Add "Real Servers"
In a production environment with more than one ADFS server, we would add the other servers as well. Of course, load balancing would make no sense with a single target server.
Adjust DNS records for ADFS (STS)
In my case, the DNS record previously pointed directly to the ADFS server at 10.0.0.41. I had already modified the record so it points to the VLM-200 load balancer:
***
In my case, since I am using ADFS 3.0, it was necessary to upgrade the VLM-200 firmware to version 7.1-22b (for VMware). Firmware is upgraded in the System Configuration | System Administration | Update Software section of the LoadMaster web interface. One simply browses for the "software update file" downloaded from the KEMP website. A reboot is required.
Configuration may vary, even with other KEMP load balancers or with other firmware versions. In case of problems, the best advice would be to contact their tech support.
Thank you for reading the article about Office 365 - Hybrid Migration - Part 7: ADFS load balancing (KEMP VLM-200) on the blog NEW TECH If you want to disseminate this article on please list the link as the source, and if this article was helpful please bookmark this page in your web browser by pressing Ctrl + D on your keyboard keys.